WinDbg官方下载:
http://msdl.microsoft.com/download/symbols/debuggers/dbg_x86_6.11.1.404.msi
http://msdl.microsoft.com/download/symbols/debuggers/dbg_amd64_6.11.1.404.msi
打开WinDbg设置Symbol File Path为:
SRV*http://msdl.microsoft.com/download/symbols然后将dump文件拖入WinDbg窗口等待片刻即有分析结果,dump文件在C:\Windows\Minidump目录。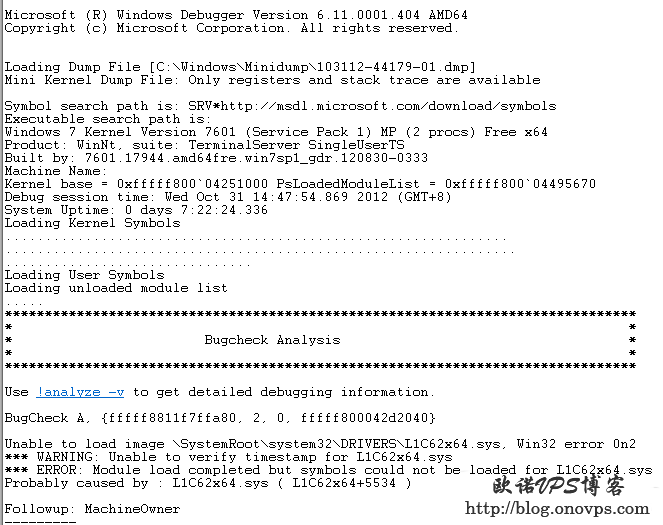
输入!analyze -v查看详细分析结果:
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: fffff8811f7ffa80, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff800042d2040, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800044ff100
fffff8811f7ffa80
CURRENT_IRQL: 2
FAULTING_IP:
nt!RtlCopyMemoryNonTemporal+40
fffff800`042d2040 4c8b0c11 mov r9,qword ptr [rcx+rdx]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: ThunderPlatfor
TRAP_FRAME: fffff88008a5e5c0 -- (.trap 0xfffff88008a5e5c0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
STACK_COMMAND: kb
FOLLOWUP_IP:
L1C62x64+5534
fffff880`05e6f534 ?? ???
SYMBOL_STACK_INDEX: c
SYMBOL_NAME: L1C62x64+5534
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: L1C62x64
IMAGE_NAME: L1C62x64.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 49d2f6fd
FAILURE_BUCKET_ID: X64_0xA_L1C62x64+5534
BUCKET_ID: X64_0xA_L1C62x64+5534
Followup: MachineOwner
---------
1: kd> lmvm L1C62x64
start end module name
fffff880`05e6a000 fffff880`05e7c000 L1C62x64 T (no symbols)
Loaded symbol image file: L1C62x64.sys
Image path: \SystemRoot\system32\DRIVERS\L1C62x64.sys
Image name: L1C62x64.sys
Timestamp: Wed Apr 01 13:09:17 2009 (49D2F6FD)
CheckSum: 0001660A
ImageSize: 00012000
Translations: 0000.04b0 0000.04e4 0409.04b0 0409.04e4可见是L1C62x64.sys的问题,查看了下是Atheros千M网卡的驱动文件,是进程ThunderPlatfor引起的系统蓝屏,先升级下网卡驱动试试,再不行就升级迅雷,郁闷ING。。。