The following packages have been kept back: proxmox-ve pve-kernel-helper
使用dist-upgrade,不要使用apt upgrade:
apt dist-upgrade 发布时间:January 4, 2024 // 分类: // No Comments
The following packages have been kept back: proxmox-ve pve-kernel-helper
使用dist-upgrade,不要使用apt upgrade:
apt dist-upgrade 发布时间:December 14, 2023 // 分类: // No Comments
宽带重新拨号会重新分配ipv6前缀,有的设备仍然优先使用旧的ip段,导致ipv6不能使用,可减小preferred_lifetime时间使旧的ip段快速失效。
openwrt dhcp提供preferred_lifetime参数设置preferred时间,需要将ra_useleasetime启用才有效,同时会将valid_lifetime修改为leasetime时间。
option leasetime '2h'
option ra_lifetime 1200
option ra_useleasetime '1'
option preferred_lifetime '10m'odhcpd源码判断设置preferred_lifetime和valid_lifetime:
src/router.c
if (addr->preferred > (uint32_t)now) {
preferred = TIME_LEFT(addr->preferred, now);
if (iface->ra_useleasetime &&
preferred > iface->preferred_lifetime)
preferred = iface->preferred_lifetime;
}
valid = TIME_LEFT(addr->valid, now);
if (iface->ra_useleasetime && valid > iface->dhcp_leasetime)
valid = iface->dhcp_leasetime;使用wireshark查看效果: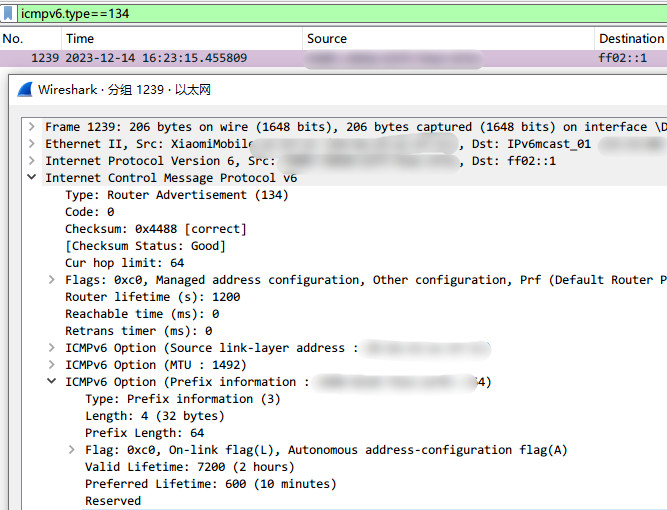
也可用tcpdump查看:
tcpdump -i br-lan -nn "icmp6 && ip6[40] == 134" -vv发布时间:December 13, 2023 // 分类: // 2 Comments
使用udpxy和msd_lite都有一些小问题,参考多方用golang写了个简单rtp多播转http单播,无缓存,cpu占用有点小高,效果不错。
package main
import (
"flag"
"fmt"
"github.com/pion/rtp"
"io"
"net"
"net/http"
//"strings"
"time"
)
var timeout = 2000 * time.Millisecond
var readbuffer = 2 * 1024 * 1024
var buffer = 1500
const (
RTP_Payload_MP2T = 33
ContentType_MP2T = "video/MP2T"
ContentType_DEFAULT = "application/octet-stream"
)
var McastIface = flag.String("m", "eth1.23", "mcast iface (IP addr or name)")
var ListenAddr = flag.String("a", "0.0.0.0", "http listen addr (default 0.0.0.0)")
var ListenPort = flag.Int("p", 8080, "http listen port (default 8080)")
func main() {
flag.Parse()
http.HandleFunc("/", handler)
fmt.Printf("http listen: %s:%d\n", *ListenAddr, *ListenPort)
err := http.ListenAndServe(fmt.Sprintf("%s:%d", *ListenAddr, *ListenPort), nil)
if err != nil {
panic(err)
}
}
var tag = "/udp/"
var tagLen = len(tag)
func handler(w http.ResponseWriter, r *http.Request) {
var err error
defer func(w http.ResponseWriter, r *http.Request) {
if err != nil {
w.WriteHeader(http.StatusInternalServerError)
io.WriteString(w, err.Error()+"\n")
}
fmt.Println(time.Now().Format("2006-01-02 15:04:05"), "close http: "+r.RemoteAddr)
}(w, r)
path := r.URL.Path
if len(path) < tagLen {
w.WriteHeader(http.StatusBadRequest)
io.WriteString(w, "No address specified\n")
return
}
addr := path[tagLen:]
fmt.Println(time.Now().Format("2006-01-02 15:04:05"), addr, r.RemoteAddr)
conn, err := newMulticastReader(addr)
if err != nil {
return
}
defer func() {
_ = conn.Close()
fmt.Println(time.Now().Format("2006-01-02 15:04:05"), "close udp: "+addr)
}()
w.Header().Set("X-Content-Type-Options", "nosniff")
conn.SetReadBuffer(readbuffer)
headerSent := false
p := &rtp.Packet{}
var buf = make([]byte, buffer)
for {
conn.SetReadDeadline(time.Now().Add(timeout))
n, err := conn.Read(buf)
if err != nil {
fmt.Println("read err:", err)
w.WriteHeader(http.StatusInternalServerError)
io.WriteString(w, err.Error())
return
}
//fmt.Println(time.Now(), n, "buf len:", len(buf))
if err = p.Unmarshal(buf[:n]); err != nil {
fmt.Println("unpack err:", err)
return
}
if !headerSent {
headerSent = true
if p.PayloadType == RTP_Payload_MP2T {
w.Header().Set("Content-Type", ContentType_MP2T)
} else {
w.Header().Set("Content-Type", ContentType_DEFAULT)
}
w.WriteHeader(http.StatusOK)
}
if _, err = w.Write(p.Payload); err != nil {
return
}
}
}
func newMulticastReader(address string) (conn *net.UDPConn, err error) {
addr, err := net.ResolveUDPAddr("udp", address)
if err != nil {
return
}
//fmt.Printf(time.Now().Format("2006-01-02 15:04:05")+" multicast: listen addr %s\n", address)
iface, err := net.InterfaceByName(*McastIface)
conn, err = net.ListenMulticastUDP("udp", iface, addr)
if err != nil {
panic(err)
}
return
}参考:
https://github.com/hello-xnew/gdpxy
https://github.com/darren/retv
发布时间:December 5, 2023 // 分类: // No Comments
修改密码后依旧如此,修改/etc/shadow用户第三个字段为正整数即可:
cat /etc/shadow
user:$1$ercaZtGB$S8x9tyPTC1Bd8Litu7irt/:17000:0:99999::::https://blog.csdn.net/baidu_31381143/article/details/53976386
发布时间:December 5, 2023 // 分类: // No Comments
由于移动默认使用password认证,先开启telnet http://192.168.1.1/system.cgi?telnet,通过telnet登录切换到电信界面用loid认证,只要olt认证成功,配置手工创建,此猫固件不包含联通界面。
ritool set Custom AH重启后在web界面恢复出厂设置,电信用户名: telecomadmin密码: nE7jA%5m,移动用户名:CMCCAdmin 密码:aDm8H%MdA
ttl连接,电路板正面网口朝上,ttl针脚从上面开始依次为RX,TX,GND
启动后进入shell:
enable
shell
LA(ImvZx%8https://www.chinadsl.net/forum.php?mod=viewthread&tid=172429
https://blog.ylx.me/archives/691.html